Teraterm Macro How to use Tera Term for the Serial Console An RS-232 serial console allows the DNP/2486 Linux to be controlled from a terminal or a PC with a terminal emulation program attached to the asynchronous COM1 serial port. Tera Term Macro language file for GeSHi. This version of ttl.php was created for Tera Term 4.60 and LogMeTT 2.9.4. Newer versions of these application can contain additional Macro commands and/or keywords that are not listed here. The latest release of ttl.php can be downloaded from Download section of LogMeTT.com.
| Home | Switchboard | Unix Administration | Red Hat | TCP/IP Networks | Neoliberalism | Toxic Managers |
| May the source be with you, but remember the KISS principle ;-) Skepticism and critical thinking is not panacea, but can help to understand the world better | ||||||
| News | Telnet Clients | Recommended Links | Teraterm Macros | Reference for macrolanguage | Invoking Teraterm from command line | Highlights of enhancements in latest versions |
| Teraterm log and replay function | Using different backgound for different servers in Teraterm | SSH | Password-less SSH login | TTSSH | Using Pageant for authentication | |
| CygTerm+ | Exceed HostExplorer | Putty | Telnet protocol | Teraterm connect command | LogMeTT | TTPMenu |
| Expect | GNU Screen | Tips | Admin Horror Stories | Unix History | Humor | Etc |
Teraterm is a very important program for any Unix system administrator. So even a little time spend to study it and to adopt better configuration brings great dividends. While colors used and size of the screen necessary is highly idiosyncratic, there are still many common themes and problems for which the following tips might be useful:
- Double clicking on .TTL file doesn't always launch macro. You need to associate the correct program with this extension. Sometimes teraterm.exe is associated instead of ttpmacro.exe. That leads to troubles.
- The way Teraterm presents the list of sites to which you connected is OK if this is just a dozen servers, but became troublesome if this is several dozens. It does not allow any hierarchy -- it is a flat list and wrong attempts are also recorded in it. This is a serious drawback in case the list in large.
In the latter case you can extract the list from TERATERM.INI. They are located close to the end of the file, starting with the line [Hosts] andhave the format like that
You can extract them using egrep and then cut them at '=' to extract the DNS names of each server and then convert into connect string. Which allow you to generates as many macros as you you have defined hosts (in simplest case macro is just a one-liner with just connect command) that login to each server you administer. In the simplest form such script can be create using xargs command. Something along the lines
- You can specify initial terminal size, for example 184 x 56 in Setup/Terminal. It makes sense to specify several predefined sized that suit you display size and selected font (full screen size, half-size and quarter-size to allow stacking of terminals, etc). For example:
- Manually editing teraterm.ini actually simpler than finding settings in the menu. Also it allows to change some settings that are not in menu.
- There are limited but useful SCP capabilities. They can be use for downloading a tar ball with your dot files and some config files after you just installed the server.
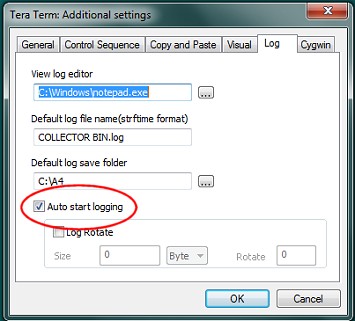
- You can log you session when using Teraterm. You can specify both Log directory name and logname (which can include strftime(3) marcos; they are the same as in Unix date function, so most sysadmin known them really well). Creating unique log filename for each instance of Teraterm is necessary if you open several terminals
- You can set an automatic timestamping of each log like via LogTimestamp=on . Usually this is not necessary as it complicates cut and paste from the log.
- See Teraterm log and replay function for more information
- If loggin is not defaut setting, you can start Teraterm with /L switch which enables logging. For that you can create a small script file
- /L=<log file>
- Authentication notes. There is a difference between SSH authenticating using 'passphrase' (the default method of authentication in Teraterm distribution) and challenge/response (keyboard interactive). Most SSH servers refuse passphrase authentication. To enable it you need to change in you /etc/ssh/sshd_config file (or equivalent) the following setting
# To disable tunneled clear text passwords, change to no here!
PasswordAuthentication yes
#PermitEmptyPasswords noYou can change the default method via Setup/SSH authentication and then selection 'use challenge/response to log in...' (or change DefaultAuthMethod=3 to DefaultAuthMethod=5 in teraterm.ini file)
That makes Teraterm behavior compatible with Putty where this authentication method is a default.
You can use Pageant for authentication
- With a special setting (Setup -> Additional Settings -> Copy & Paste ->DisableMouseRButtonPaste) version 4.58 (but not 4.62) understands Unix-style middle mouse button paste operation.
- Tera Term command has multiple line option, with some very useful but rarely known (for example /R replay option, /M macro file specification)
Options
- <host>
- Host name or IP address or Named pipe.
- <host>:<TCP port#>
- <host> with a TCP port number.
':' is placed between <host> and <TCP port#>. - <host> <TCP port#>
- <host> with a TCP port number.
Space character(s) between <host> and <TCP port#>.
Number just after <host> is interpreted as a port number. - telnet://<host>[:<TCP port#>][/]
- URL style - for telnet handler
TCP port number and '/' at the end are optional.
If TCP port number is omitted, use 23. (TCPPort setting in setup file is ignored.) - /B
- Telnet binary option.
- /BAUD=<baud rate>
- baud rate of serial port. If the baud rate not supported by Tera Term is specified, this option is ignored.
- /C=<serial port#>
- Serial port
- /C=1 COM1
- /C=2 COM2
- /C=3 COM3
- ... ... ...
- /C=256 COM256
- /DUPLICATE
- Internal use(must not specify this option)
- /DS
- Disable displaying the 'New connection' dialog on startup
- /E
- Disable TCPLocalEcho and TCPCRSend option
- /ES
- Enable displaying the 'New connection' dialog on startup
- /F=<setup file>
- Setup file [2]
/F=TERATERM.INI (default)
If this value is not a full path, it is understood as a relative path from ttermpro.exe. - /FD=<file transfer directory>
- File transfer directory [2]
- /H
- Hide title bar.
- /I
- Start Tera Term in iconized state.
- /K=<keyboard setup file>
- Keyboard setup file [2]
/K=KEYBOARD.CNF (default)
If this value is not a full path, it is understood as a relative path from ttermpro.exe. - /KR=<kanji code (receive)>
- Note: Japanese, Korean and UTF-8 mode only
- /KR=SJIS
- /KR=EUC
- /KR=JIS
- /KR=UTF8 UTF-8(Normalization Form C: Windows, Linux)
- /KR=UTF8m UTF-8(Normalization Form D: Mac OS X)
- /KR=KS5601 for Korean mode
- /KT=<kanji code (transmit)>
- Note: Japanese and Korean mode only
- /KT=SJIS
- /KT=EUC
- /KT=JIS
- /KT=UTF8
- /KT=KS5601 for Korean mode
- /L=<log file>
- Start Tera Term with logging. [2]
- /LA=<language>
- Language mode.
- /LA=E English
- /LA=J Japanese
- /LA=K Korean
- /LA=R Russian
- /LA=U UTF-8
- /M=<macro file>
- Start Tera Term with macro. [2]
If this value is not a full path, it is understood as a relative path from ttermpro.exe. - /MN=<multicastname>
- Multicast name for sendmulticast macro command. [2]
- /NOLOG
- Start Tera Term without logging.
- /P=<TCP port#>
- TCP port number
- /R=<replay file>
- Replay file [2]
- /T=<telnet flag>
- /T=1 Enable telnet
- /T=0 Disable telnet
- /TEKICON=<icon name>
- TEK window icon. Could be specify the same value of TEKIcon of setup file.
- /TIMEOUT=<connecting timeout value>
- Could be specified per seconds.
- /V
- Start Tera Term in hidden (invisible) state.
- /VTICON=<icon name>
- VT window icon. Could be specify the same value of VTIcon of setup file.
- /W=<window title>
- Window title [2]
A user should put the window title in quotations by using `' character two times to include the character. - /X=<window position (x)>
- Windows position (horizontal)
- /Y=<window position (y)>
- Windows position (vertical)
- /NAMEDPIPE
- Named pipe(<ServerName>pipe<PipeName>)
- /AUTOWINCLOSE=<flag>
- AutoWinClose
- /AUTOWINCLOSE=on Automatically close the window on disconnection.
- /AUTOWINCLOSE=off Do not close the window on disconnection.
- ;<comment>
- Comment. Should be last in the command line.
Examples
Default values
Following default values are stored in the Tera Term setup file:
Notes
[1] Only if <telnet flag> is 1 (on) and <TCP port#> is 23, Tera Term starts spontaneously sending telnet commands to the host for the option negotiation when the TCP/IP connection is established. In any cases, Tera Term can respond to telnet commands sent by the host.
[2] Quote the multicast name when the name includes the space and `' character. And then, a user should put the window title in quotations by using `' character two times to include the character.
NEWS CONTENTS
- 20141120 : TeraTerm Macro language for dummies (or something like that) ( Oct 21, 2012 , TeraTerm Support Forums )
- 20141120 : Log and replay functions ( Log and replay functions, )
- 20141120 : Vim Control Sequence Example ( Vim Control Sequence Example, )
- 20141120 : Tips on telnet connection with a port other than 23 ( Tips on telnet connection with a port other than 23, )
- 20141120 : Log and replay functions ( Log and replay functions, )
Old News ;-)
| Switchboard | |||||
| Latest | |||||
| Past week | |||||
| Past month | |||||
[Nov 20, 2014] TeraTerm Macro language for dummies (or something like that)
Oct 21, 2012 | TeraTerm Support Forums
Location: WisconsinSo I'm attempting to consolidate what I know of the TeraTerm language into a single mega-post. If you have any knowledge that you think would be a valuable addition to this post, feel free to let me know.
Note that this is pretty much just an abridged form of the language reference tied into a somewhat cohesive format. Just because something isn't mentioned here doesn't mean it doesn't exist; check out the official language reference and search the forums to get a handle on some of TeraTerm's more advanced features. This is really not a full-fledged tutorial to take you from the very basics of computer literacy; if you have no prior programming experience this may be challenging to follow.
As a little precursor, if you happen to use Programmer's Notepad as your editor of choice, the NSIS Installer highlighting scheme matches fairly well with this scripting language. Vim users might be able to make use of this highlighting scheme (somewhat outdated, won't have latest keywords).
TeraTerm basics
So to start things off, let's deal with variables.
There are two types of variables: Strings (limited to 255 characters) , and Integers (Limited to ~ +/-2 billion) (want to go bigger?). The type is determined implicitly when the variable is created and cannot be altered afterwards.
Also, since TeraTerm 4.72, there are now arrays of both of these types (limited to 65536 indices per array)
- integerVariable=10 ; An Integer variable
- strVariable='asdf' ; A string variable
- strVariable2='0' ; Still a string variable
- integerVariable='asdf' ; ERROR!!!!!!
- integerVariable=2
- ; A little fun with arrays:
- intdim integerArray 10 ; Create an integer array of size 10
- integerArray[0]=10 ; Assigns the first element of the array to 0
- integerArray[10]=10 ; ERROR!!!!!
- ; It's almost exactly the same for strings, just using strdim instead:
- strdim strArray integerVariable ; Creates a string array that has the size given in integerVariable
- ; Also, by the way, the semicolon (;) is the character that denotes a comment; anything after it in a line has no effect on the running of your script (notice how I used the semicolon in a grammatically correct way in a sentence about semicolons ;-)
But variables by themselves are boring. The real basis of any programming language is the if statement. However an if statement by itself is somewhat boring, so let's go a little further and also show you a wait statement:
- wait 'value = 0' 'ERROR'
- if result=1 then
- ; value = 0 was received on the terminal
- elseif result=2
- ; ERROR was received on the terminal
- endif
The wait statement is one of the more or less unique features of TeraTerm. Essentially, it reads through all of the serial output that hasn't been parsed yet, and when one of the strings in its sensitivity list is found, it sets result to the index of that string and moves on. The documentation for the setsync command has a partial general overview for how TeraTerm internally works.
Note that you can also set a timeout for wait, and it will then only hold up the execution of the script for at most timeout.mtimeout seconds:
- timeout=1
- mtimeout=500 ; Set the timeout for 1.5 seconds
- wait 'Good' 'Bad'
- if result=0 then
- ; Neither good nor bad appeared in the terminal output during the 1.5 seconds
- endif
A nice counterpoint to the 'wait' command is the 'sendln' and 'send' commands. These guys do pretty much what their names suggest: they write stuff back out to the terminal (with sendln adding a newline at the end of its string). A common use that I have for the wait/sendln pair is to send a series of commands to a machine. For example, when sending a series of commands to a Linux box, it might look something like the following:
- wait 'root@localhost#'
- sendln 'command'
- wait 'root@localhost#'
- sendln 'command'
- wait 'root@localhost#'
- sendln 'command'
This ensures that the prior command has finished before you send the next command. The sendkcode command is also occasionally useful in some cases.
Note that the above code is somewhat ugly. If the prompt were to change (say from root@localhost to root@servername), I'd have to manually replace a bunch of lines. Since I'm lazy, the following format is much nicer:
- cmdPrompt='root@localhost'
- wait cmdPrompt
- sendln 'command'
- wait cmdPrompt
- sendln 'command'
- wait cmdPrompt
- sendln 'command'
 That looks much nicer.
That looks much nicer.Looping
Branching is all well and good, but eventually you will want to do something that has some repetition in it. Teraterm has several more or less standard looping constructs
- do while i>0
- i = i - 1
- loop
- do
- i=i-1
- loop while i>0
- for j 1 10
- i=j+i
- next
- until i > 10
- i = i + 1
- enduntil
- while i>0
- i = i - 1
- endwhile
I won't go into too much detail about all of these; TeraTerm probably has more looping constructs than is really healthy, but definitely keep in mind the 'for' loop, and the fact that the 'do while' loop can be done as a pre-test loop or a post-test loop. The 'break' command can also be used to escape from a loop before its condition triggers
Lastly for the basics is TeraTerm's goto command. Some people (especially those experienced with C and who have experienced the nightmares of spaghetti code) view gotos as positively evil and wish they could be nuked from every language in existence. Gotos can do just about anything, but typically not as nicely as one of the above looping structures. About the only place that gotos should really go is in error handling:
- wait 'Good' 'Bad'
- if result=2 goto ERROR
- ; Presumably, a bunch of non-related code goes here
- exit ; Typically, you don't want to execute the error code upon successful completion of the normal code, so this exits before doing that
- :ERROR
- ; Error-handling/messaging code goes here
- exit
TeraTerm and regular expressions
Regular expressions are an interesting creature in and of themselves. An old and relatively well-known quote about regular expressions (regexes) goes something like this:
Quote:
Some people, when confronted with a problem, think 'I know, I'll use regular expressions.' Now they have two problems.
Regexes are a double-edged sword that allow you to do stuff with strings that would normally not be possible. Since I don't really want to go into all the nitty gritty, here's a link to wikipedia, as well as afairly-well-laid-out regex tutorial site. Note that TeraTerm has also posted a reference for the regex engine that they use, but that isn't really laid out for learning...
TeraTerm has several commands which use the power of regular expressions (let me know which one's I'm forgetting...):
- waitregex <string1 with regular expression> [<string2 with regular expression> ...]
- strmatch <target string> <string with regular expression>
- strreplace <strvar> <index> <regex> <newstr>
strmatch and strreplace are both relatively normal. You put your regular expression in, and TeraTerm works its magic.
waitregex is a beast that I've seen misused in these forums time and again. In many ways, it is identical to the wait command, just with regular expression support. The large difference is with regular expression matching. Regular expression matching is what happens when a regular expression with parenthesis triggers on a string. The result inside the string is then returned (in normal regular expressions, it is returned as 1, 2, 3, etc, while with TeraTerm, they are stored in the groupmatchstr1, groupmatchstr2,...,groupmatchstr9 variables).
An example is as follows:
- waitregex 'value = ([0-9]+)' 'ERROR'
- if result=1 then
- str2int returnValue groupmatchstr1
- endif
Let's pick the above code fragment apart bit by bit.
First we have '[0-9]+' This regex essentially grabs the largest amount of consecutive characters that fall between 0 and 9. The parenthesis '(...)' are what initiate the grouping. With the parenthesis, the string that was caught by '[0-9]+' gets stored into groupmatchstr1. If the regular expression as a whole was triggered, the result will be one and the if statement will let the str2int command work its magic. The str2int command (and its counterpart, the int2str command) do exactly what their names suggest: convert between string and integer variables.
Thus, if the 'value = 5643' was received on the terminal, this code would set returnValue to 5643
Note that waitregex only works on the first 255 characters of a line, so anything further than that and you're going to have to find another way.
File input and output
My file I/O skills are minimal at best. Anything that you'd care to offer is gladly accepted
Also, don't forget about the ability to use logging commands in some cases (check out loginfo, logopen, logclose, logstart, logpause, and logwrite)
User input and output
Most of the commands used here are described in the Miscellaneous Commands section of the TTL Command Reference.
- messagebox <message> <title>
This is one of the most commonly-used UI-type commands of the macro language. It pops up a window with the title equal to <title>, and the content equal to <message>, with an Ok button at the bottom. Note that code beneath this command won't execute until Ok is clicked.
- yesnobox <message> <title>
This is almost identical to the messagebox, however rather than an Ok button, there's a Yes and a No button. If Yes is clicked, result=1, otherwise result=0
- inputbox <message> <title> [<default>]

The third of the *box commands that I use on a normal basis, this is like the messagebox command, but with an area that the user can type stuff in. That area is populated with <default> when the window first appears, and after the user clicks Ok, the variable 'inputstr' contains the value of that area.
Strings!!!
Fill this section with stuff for commands like sprintf2
Connecting to things other than serial ports and whatnot
I'm really not at all good with TeraTerm in this department. If someone else here has some wisdom to offer, feel free to drop it off here...
Any feedback is appreciated, both for my sake, and for all of the newbies out there. The main goal of this post is to be a one-stop learning reference for people who are just learning the language, as well as to facilitate the general usability of it through simple examples.
Good luck, bon apetit, hasta la vista, whatever. Just go out and make/break something...
Changelog:
10/24/2012 - Added a brief (unverified) description of arrays (I use a slightly older version of TT at work, and primarily use Linux at home currently, so I haven't had a chance to play around with these)
10/31/2012 - Added more formatting/hyperlinks and clarified a few points
Let's keep the suggestions coming!
_________________
If one of my posts helped you out, do me a favor:
Next time anyone asks you for help, go out of your way to help them.
Thanks!
Log and replay functions
You can save the host data to the file if you use Tera Term logging function.
Log to the file
You can log characters received from the host. Execute the [File] Log command to start logging.
Do in the following commands:
- Do [File] Log command.
- 'Tera Term: Log' dialog box will be shown.
Input the saving file name to `File Name:'.
All host data will be written to the file if you check `Binary' option.
KANJI, CR and LF codes are converted to host character code, written to the file if you uncheck `Binary' option. However, the escape sequences are not written to the file.
The host data will append the file if you check `Append' option.
The host data will overwrite the file if you uncheck `Append' option. - Push OK button, 'Tera Term: Log' icon will be shown. And logging will start.
- Push Close or Pause button on the logging dialog box if you finish the logging or temporarily stop. Pause button will change into Start button if you push Pause button, the logging will restart.
To browse log files, which contain escape sequences, it is convenient to use the replay function of Tera Term. To replay a log file.
Replay the log file
Run Tera Term with command line in the following:
Tera Term analyzes the specified log file and understands the escape sequence datas. If so, the contents of log file will be displayed in Tera Term window as if the characters were received from the host. We call this function 'replay log'.
And also, you can also use 'Host:' on the [File] New connection command.
Tera Term Macro Examples Biology
Vim Control Sequence Example
Auto indent can be disabled on pasting from clipboard
Basically, the host application can not recognize the difference between the user input and pasting from clipboard. However, when a user uses the Bracketed Paste Mode as the xterm extension, the application can recognize its difference and a user can change the behavior of pasting from clipboard.
The vim configuration is described below. The following will use xterm's bracketed paste mode to make pasting automatically enable paste mode and insert mode. Also works fine in ~/.vimrc file.
When a user pastes at the normal mode by using the above configuration, the mode will be automatically changed to the insert mode and do the paste. If this behavior is denied, use the below configuration.
Also, refer to the GNU Screen Notice.
The vim editor can automatically recognize the terminal color number, namely the 256 color supporting because the Tera Term 4.83 or later supports the Termcap String Query of xterm. So, a user must properly configure the background setting to draw the highlight color regarding the vim background color.
When the background color is the dark color(i.e, black), specify the dark setting. Also, when the background color is the bright color(i.e, white), specify the light setting.
With above setting, the vim can know the terminal background color. So, if the configuration is mistaken, the highlight color will be indistinct because the text and the background color is almost same.
If the vim automatic recognition of color is stopped, add the set t_RV= entry in the .vimrc file. However, the automatic recognition of mouse type is stopped.
Also, refer to the :help 'background' on the vim editor for details.
Tips on telnet connection with a port other than 23
On the command line, or on the [File] New connection dialog box, you can specify the TCP port number (<TCP port#>) and telnet flag (<telnet flag>) for a TCP/IP connection. If these parameters are omitted in the command line, the default values are taken from the Tera Term setup file.
Only if <telnet flag> is 1 (on) and <TCP port#> is 23, Tera Term starts spontaneously sending telnet commands to the host for the option negotiation when the TCP/IP connection is established.
This particular port number for telnet, 23, can be changed by editing the TelPort line in the [Tera Term] section of setup file like the following:
Log and replay functions
You can save the host data to the file if you use Tera Term logging function.
Log to the file
You can log characters received from the host. Execute the [File] Log command to start logging.
Do in the following commands:
- Do [File] Log command.
- 'Tera Term: Log' dialog box will be shown.
Input the saving file name to `File Name:'.
All host data will be written to the file if you check `Binary' option.
KANJI, CR and LF codes are converted to host character code, written to the file if you uncheck `Binary' option. However, the escape sequences are not written to the file.
The host data will append the file if you check `Append' option.
The host data will overwrite the file if you uncheck `Append' option. - Push OK button, 'Tera Term: Log' icon will be shown. And logging will start.
- Push Close or Pause button on the logging dialog box if you finish the logging or temporarily stop. Pause button will change into Start button if you push Pause button, the logging will restart.
To browse log files, which contain escape sequences, it is convenient to use the replay function of Tera Term. To replay a log file.
Replay the log file
Run Tera Term with command line in the following:
Tera Term analyzes the specified log file and understands the escape sequence datas. If so, the contents of log file will be displayed in Tera Term window as if the characters were received from the host. We call this function 'replay log'.
Tera Term Macro Ssh Example
And also, you can also use 'Host:' on the [File] New connection command.
Recommended Links
Google matched content |
Softpanorama Recommended
Top articles
Sites
Top articles
Sites
Etc
Society
Groupthink :Two Party System as Polyarchy : Corruption of Regulators :Bureaucracies :Understanding Micromanagers and Control Freaks : Toxic Managers : Harvard Mafia :Diplomatic Communication : Surviving a Bad Performance Review : Insufficient Retirement Funds as Immanent Problem of Neoliberal Regime : PseudoScience :Who Rules America :Neoliberalism : The Iron Law of Oligarchy : Libertarian Philosophy
Quotes
War and Peace: Skeptical Finance : John Kenneth Galbraith :Talleyrand :Oscar Wilde :Otto Von Bismarck :Keynes :George Carlin :Skeptics :Propaganda : SE quotes : Language Design and Programming Quotes :Random IT-related quotes : Somerset Maugham :Marcus Aurelius :Kurt Vonnegut :Eric Hoffer :Winston Churchill :Napoleon Bonaparte :Ambrose Bierce : Bernard Shaw : Mark Twain Quotes
Bulletin:
Vol 25, No.12 (December, 2013) Rational Fools vs. Efficient Crooks The efficient markets hypothesis :Political Skeptic Bulletin, 2013 :Unemployment Bulletin, 2010 : Vol 23, No.10 (October, 2011) An observation about corporate security departments :Slightly Skeptical Euromaydan Chronicles, June 2014 :Greenspan legacy bulletin, 2008 :Vol 25, No.10 (October, 2013) Cryptolocker Trojan (Win32/Crilock.A) :Vol 25, No.08 (August, 2013) Cloud providers as intelligence collection hubs : Financial Humor Bulletin, 2010 :Inequality Bulletin, 2009 :Financial Humor Bulletin, 2008 :Copyleft Problems Bulletin, 2004 :Financial Humor Bulletin, 2011 :Energy Bulletin, 2010 : Malware Protection Bulletin, 2010 : Vol 26, No.1 (January, 2013) Object-Oriented Cult :Political Skeptic Bulletin, 2011 :Vol 23, No.11 (November, 2011) Softpanorama classification of sysadmin horror stories : Vol 25, No.05 (May, 2013) Corporate bullshit as a communication method : Vol 25, No.06 (June, 2013) A Note on the Relationship of Brooks Law and Conway Law
History:
Fifty glorious years (1950-2000): the triumph of the US computer engineering :Donald Knuth : TAoCP and its Influence of Computer Science : Richard Stallman : Linus Torvalds :Larry Wall :John K. Ousterhout : CTSS : Multix OSUnix History : Unix shell history :VI editor :History of pipes concept :Solaris : MS DOS : Programming Languages History :PL/1 : Simula 67 :C :History of GCC development : Scripting Languages :Perl history :OS History : Mail :DNS : SSH : CPU Instruction Sets :SPARC systems 1987-2006 :Norton Commander :Norton Utilities :Norton Ghost :Frontpage history :Malware Defense History :GNU Screen : OSS early history
Classic books:
The Peter Principle : Parkinson Law : 1984 :The Mythical Man-Month : How to Solve It by George Polya :The Art of Computer Programming :The Elements of Programming Style :The Unix Hater’s Handbook :The Jargon file :The True Believer :Programming Pearls :The Good Soldier Svejk : The Power Elite
Most popular humor pages:
Manifest of the Softpanorama IT Slacker Society :Ten Commandments of the IT Slackers Society : Computer Humor Collection : BSD Logo Story :The Cuckoo's Egg :IT Slang : C++ Humor : ARE YOU A BBS ADDICT? :The Perl Purity Test :Object oriented programmers of all nations : Financial Humor :Financial Humor Bulletin, 2008 : Financial Humor Bulletin, 2010 : The Most Comprehensive Collection of Editor-related Humor : Programming Language Humor :Goldman Sachs related humor :Greenspan humor : C Humor :Scripting Humor :Real Programmers Humor :Web Humor : GPL-related Humor : OFM Humor :Politically Incorrect Humor :IDS Humor : 'Linux Sucks' Humor : Russian Musical Humor : Best Russian Programmer Humor : Microsoft plans to buy Catholic Church : Richard Stallman Related Humor :Admin Humor : Perl-related Humor : Linus Torvalds Related humor : PseudoScience Related Humor :Networking Humor :Shell Humor :Financial Humor Bulletin, 2011 : Financial Humor Bulletin, 2012 :Financial Humor Bulletin, 2013 : Java Humor : Software Engineering Humor : Sun Solaris Related Humor :Education Humor : IBM Humor : Assembler-related Humor :VIM Humor : Computer Viruses Humor : Bright tomorrow is rescheduled to a day after tomorrow : Classic Computer Humor
The Last but not LeastTechnology is dominated by two types of people: those who understand what they do not manage and those who manage what they do not understand ~Archibald Putt. Ph.D
Copyright © 1996-2020 by Softpanorama Society. www.softpanorama.org was initially created as a service to the (now defunct) UN Sustainable Development Networking Programme (SDNP) without any remuneration. This document is an industrial compilation designed and created exclusively for educational use and is distributed under the Softpanorama Content License. Original materials copyright belong to respective owners. Quotes are made for educational purposes only in compliance with the fair use doctrine.
FAIR USE NOTICEThis site contains copyrighted material the use of which has not always been specifically authorized by the copyright owner. We are making such material available to advance understanding of computer science, IT technology, economic, scientific, and social issues. We believe this constitutes a 'fair use' of any such copyrighted material as provided by section 107 of the US Copyright Law according to which such material can be distributed without profit exclusively for research and educational purposes.
This is a Spartan WHYFF (We Help You For Free) site written by people for whom English is not a native language. Grammar and spelling errors should be expected. The site contain some broken links as it develops like a living tree...
Tera Term Macro Examples
| You can use PayPal to to buy a cup of coffee for authors of this site |
Disclaimer:
The statements, views and opinions presented on this web page are those of the author (or referenced source) and are not endorsed by, nor do they necessarily reflect, the opinions of the Softpanorama society.We do not warrant the correctness of the information provided or its fitness for any purpose. The site uses AdSense so you need to be aware of Google privacy policy. You you do not want to be tracked by Google please disable Javascript for this site. This site is perfectly usable without Javascript.
Last modified:July 28, 2019
I’m using Tera Term for login and work on a server. And, I feel it is annoying to login manually.
Tera Term has the macro functionality. So, it can login to server by only Double Click by some settings.
In this article, I introduce how to auto login by Tera Term macro.
【Step1】Associate with macro file(.ttl file)
The macro file extension is “.ttl”. So, to set file association to execute Tera Term macro(ttpmacro.exe) by double click .ttl file.
The following the article is useful, please see.
https://www.lifewire.com/how-to-change-file-associations-in-windows-2624477
【Step2】Create macro file(.ttl file)
This is a sample .ttl file.
Change the following setting depending on your environment.
- username:User name to login
- password:User password
- hostname:Server host name or IP address
- logfilename:Log file name (entered command and output is written)
- /auth:How to authenticate
- logdir:Output folder of log fil
Create .ttl file, then double click to check login to server!!
Tera Term Macro File
…((((*ФωФ)ノ Go Go ♪